What is a Virtual Private Network (VPN), what does it do, and do you need one?
Content
A VPN (virtual private network) service encrypts and anonymizes your internet traffic to ensure that your sensitive data is safely transmitted, and your online identity is protected.
Before we start: This article is our balanced and unbiased take on the VPN ecosystem. We are not making any recommendations and we are not linking to any VPN affiliate programs.
VPNs have quickly gained popularity as a security and privacy tool for regular Internet users. Commercial VPNs are now a multi-billion global industry with numerous VPN providers, and apps available for every computing platform and device category.
It’s called virtual because you don’t need to install any hardware; a VPN is a software tool that you download onto your device and then configure for your use. It’s called private network because extends the security of a private network (i.e., a computer network that uses a private address space of IP addresses) across a public network (the Internet) and enables users to send and receive data across as if their computing devices were directly connected to the private network.
This means that a VPN is created by establishing a virtual point-to-point connection through the use of dedicated circuits or with tunneling protocols over existing networks. A VPN available from the public Internet can provide some of the benefits of a wide area network (WAN).
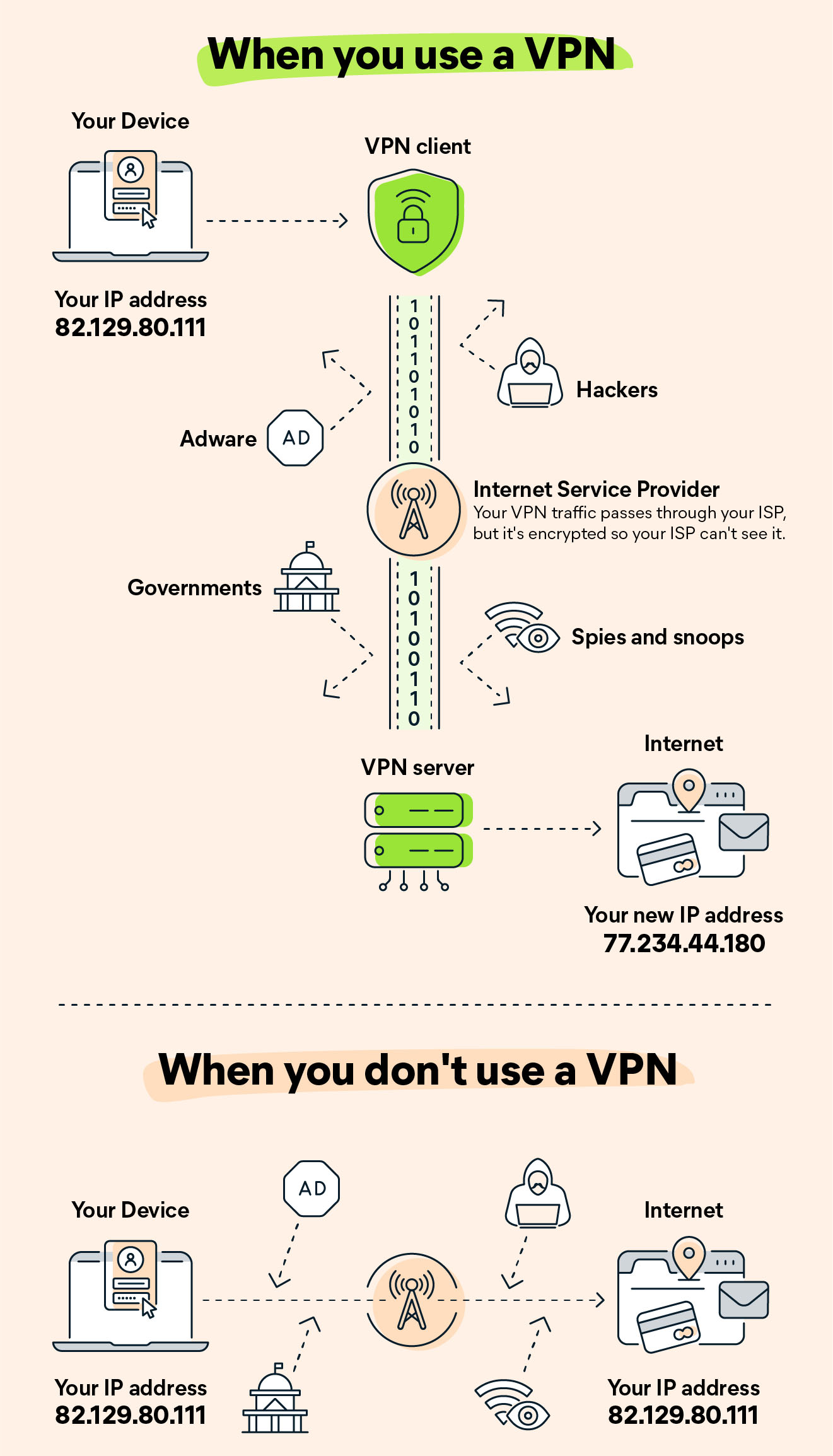
When you access a site through a VPN server, the source of your connection is shown as one of the (often many) routers of the VPN service - called a proxy server - not your own. This means that the owners of the site, and anyone else trying to spy on you, cannot deduce who you are.
Why is the purpose of a VPN and how does it protect you?
VPN services create a secure connection, often called a ‘tunnel’, to a secure server from the VPN service that then connects you to your intended destination. This tunnel typically provides an extra layer of encryption that serves as protection from surveillance by the intermediate networks, bypasses access restrictions active in those networks, and hides your actual IP address (and location) from their destination service.
VPNs were initially developed in 1996 by Microsoft as a peer-to-peer tunnelling protocol to facilitate private communication in enterprise settings. In these early days, VPNs provided a way to create private connections between computers and transfer data between them securely over the public Internet. These are still the guarantees that VPNs provide for general users today.
A VPN is one of the best tools for your privacy when surfing the Internet by encrypting your connection. This keeps your IP address hidden from the websites that you access and provides you with an extra layer of privacy and anonymity.
The result is that your browsing and search activity (and history) is hidden from your Internet Service Provider (ISP). The only thing the ISP can see is your encrypted traffic traveling to the VPN server.
Since your IP address gives away your physical location, you also can change your online location by connecting through your VPN’s server in a different country (in theory, that is. Read more below in the section: False claims by VPNs).
Why use a VPN?
Exposure to risk of surveillance, reports of Internet Service Providers (ISPs) selling data and increasing access restrictions have all led to an increased awareness of online risks for Internet users. VPNs are marketed as technological solutions to many of these issues, though not all users will be able to verify these claims.
Internet users worldwide rely on commercial network proxies both to conceal their true location and identity, and to control their apparent location. Their reasons range from mundane to security critical.
Concealing your identity is especially important if you regularly connect to public Wi-Fi networks such as in airports, coffee shops or public buildings. You never know who might be monitoring your internet traffic and what they might steal from you, including passwords, personal data, payment information, or even your entire identity.
Benefits of a VPN
Encrypted connection
The benefits of a VPN include increased security thanks to an encrypted connection and sometimes even speed (because your ISP can’t throttle your bandwidth anymore).
Disguised whereabouts and regional content
Since you now can access the Internet from other locations, your actual location cannot be determined. You might also be able to access regional services and websites that you can’t access from your actual location (this, however, doesn’t always work with all services).
Secure data transfer
If you work remotely and need to access important files on your company’s network, in most cases you can gain access to the corporate network only with a secure connection. VPN services connect to private servers and use encryption methods to reduce the risk of data leakage.
Essential features to look for when choosing a good VPN
Speed, price, and an easy-to-use app with hassle-free configuration settings are among the top three requirements in a VPN. Other requirements, depending on users’ needs, are variety or number of servers, and using a VPN to change country location for media sites such as Netflix. The key requirements for any good VPN are:
Encryption of your IP address
The most critical task for any VPN is to hide your IP address from your ISP and other third parties. This allows you to send and receive information online without the risk of anyone but you and the VPN provider seeing it.
Encryption of protocols
A VPN should prevent you from leaving traces, for example, in the form of your internet history, search history and cookies. The encryption of cookies is especially important because it prevents third parties from gaining access to confidential information such as personal data, financial information and other content on websites.
Kill switch
If your Internet connection via a VPN is suddenly interrupted, your secure connection will also be terminated. A good VPN can detect this sudden downtime and terminate preselected programs, reducing the likelihood that data is compromised.
Multi-factor authentication
By using a variety of authentication methods, a strong VPN checks everyone who tries to log in. For example, you might be prompted to enter a password, after which a code is sent to your mobile device. This makes it difficult for third parties to access your secure connection.
Pricing
VPNs offer different subscription models: paid/premium services, free to use services, and freemium models that offer limited free features and charge for premium features and services.
Free VPN service providers do not tell you how they make money. Usually, they are displaying ads, but some sneaky free providers leak your information to third parties to make money.
If you don’t want to compromise your connection quality and security, consider choosing a paid VPN plan.
Any reputable service will give you a free trial period or lets you terminate with a full refund within the first week or month.
VPN security – what types of secure VPNs are there?
Commercial VPN providers make use of one of the available VPN protocols such as OpenVPN, L2TP, IPSec, IKEv2, and Wireguard, or develop proprietary protocols, which are typically extensions of existing ones, optimized to fit their particular needs and business model.
There are different flavors of VPNs with the three main types being SSL (secure socket layer), site-to-site, and client-to-server. These VPNs are usually employed by companies that need to grant employees and others secure access to organizational resources.
Are VPNs really secure?
Although they protect your IP and encrypt your internet history, a VPN connection does not protect your computer from outside intrusion such as Trojans, viruses, bots or other malware. For example, no matter if your connection is secure, if you download infected email and click on a malicious link, you still are at risk.
Once the malware has found its way onto your device, it can steal or damage your data, whether you are running a VPN or not. It is therefore important that you use a VPN together with a comprehensive anti-virus program to ensure maximum security.
How to install a VPN and configure VPN settings
For standalone VPN clients you need to install software that you download from the VPN service’s website. When setting up the VPN, one endpoint executes the VPN link and connects to the other endpoint, creating the encryption tunnel.
There is also the possibility to add a VPN browser extension to most popular web browsers. While browser extensions are not quite as comprehensive as VPN clients, they may be an appropriate option for occasional internet users who want an extra layer of internet security. Some browsers, including Opera, even have their own integrated VPN extensions. Extensions make it easier for users to quickly switch and configure their VPN while surfing the internet. However, the VPN connection is only valid for information that is shared in this browser. Using other browsers and other internet uses outside the browser (for instance online games) cannot be encrypted by the VPN.
If multiple devices are connected to the same internet connection, it may be easier to implement the VPN directly on the router rather than to install a separate VPN on each device. A router VPN is especially useful if you want to protect devices with an internet connection that are not easy to configure, such as smart TVs. They can even help you access geographically restricted content through your home entertainment systems.
Apart from web browsers, there are a number of VPN options for smartphones and other internet-connected devices such as smart TVs. Expect a good VPN provider to offer mobile solutions, which can be downloaded directly from Google Play or the Apple App Store.
Are VPNs legal?
VPNs are legal to use in all free societies but a number of more autocratic and totalitarian governments either regulate or outright ban and block VPNs: Belarus (complete ban), China (tightly regulated), Iraq (complete ban), Iran (tightly regulated), North Korea (complete ban), Oman (complete ban), Russia (complete ban), Syria (partially blocked), Turkey (complete ban), Turkmenistan (complete ban), Uganda (partially blocked), and the U.A.E. (tightly regulated). Still, others impose internet censorship laws, which makes using a VPN risky.
One thing to remember is that in countries where VPNs are legal, committing criminal acts or merely visiting sites that the government has strictly banned still is illegal, VPN or not.
Misconceptions about VPNs
A VPN does not make your Internet ‘private’. You can still be tracked through tracking cookies and device fingerprinting, even if your IP address is hidden.
A VPN does not make you immune to hackers.
A VPN does not have to be difficult to configure. The leading VPNs have a have a clean and intuitive user interface.
VPNs are not just for criminals and hackers.
Except in some countries (the usual suspects), VPNs are not illegal.
Even if you have nothing to hide you will benefit from a VPN. VPN isn’t only for privacy. It is a security tool that helps prevent hacking and protect your data from snoopers.
Despite being a privacy-protection tool, VPN does not guarantee 100% protection. Security breaches are not unusual.
False claims by VPNs
In simple terms, a user using a VPN is simply transferring trust from their Internet service provider onto the VPN provider. ISPs have been around for longer and have many regulations globally. However, such regulations and advocacy has not yet caught up to the VPN industry.
For instance, proxy operators offer no proof that their advertised server locations are accurate. IP-to-location databases tend to agree with the advertised locations, but there have been many reports of serious errors in such databases.
In a study presented at the Internet Measurement Conference in 2018 ("How to Catch when Proxies Lie: Verifying the Physical Locations of Network Proxies with Active Geolocation"), scientists estimated the locations of 2269 proxy servers from ping-time measurements to hosts in known locations, combined with AS and network information. These servers are operated by seven proxy services, and, according to the operators, spread over 222 countries and territories. Our measurements show that one third of them are definitely not located in the advertised countries, and another third might not be. Instead, they are concentrated in countries where server hosting is cheap and reliable (e.g., Czech Republic, Germany, Netherlands, UK, USA).
Bottomline: Although no VPN gives you 100% security, using a reputable VPN service is a good investment that encrypts and anonymizes your internet traffic, protects your online identity, and could help you get past websites' regional restrictions.

